Immutability is an important component of any backup strategy. However, as an S3 provider, immutability can often leave you with data locked for a longer term than you really want.
Immutable modes
Minio offers three different immutability modes that can be enabled on objects.
- Governance Mode
- Compliance Mode
- Legal Hold
“Compliance mode is more restrictive and cannot be undone within the retention period. As a result, Compliance mode ensures that no one, including the root user, can delete an object during its retention period.”
Which is great! This means all objects are set immutable until their immutability retention period ends. However, that also means all objects are immutable until their retention period ends. No one, not even the provider can delete the data. But what happens if the customer leaves and wants the data deleted, but the retention period has not ended.
Governance Mode
This is where Governance Mode comes into play. Veeam Backup and Replication can be enabled to utilize Governance Mode, rather than the default Compliance mode Veeam uses by default.
“Governance mode is used to protect objects from being deleted by standard users. Some users, however, will need to retain the permissions required to modify the retention settings or delete the objects. Those users will require special permissions such as the s3:BypassGovernanceRetention permission and DeleteObject permission.”
Providers of the S3 repositories can utilize Governance Mode to allow customers full immutability without the risk of retaining customer data beyond the date the customer wants no matter the reason – whether its due to accidentally setting immutability retention longer than required, or whether the customer wants to cancel the contract.
Minio Bucket
There is nothing special to set for Minio itself beyond the normal immutability settings.
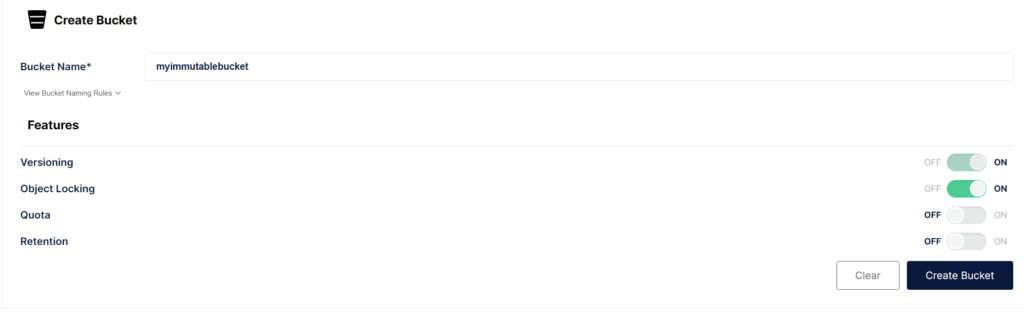
As a side note – enable the Quota to allow Veeam’s SOSAPI to display the quota size for the bucket, rather than the entire size of your Minio cluster.
Veeam Permissions
Set your policy for the bucket as below. Note, we do not give all permissions, nor do we give the very special s3:BypassGovernanceRetention permission. This is important to ensure the objects will be Immutable, and the policy does not allow for any person who accesses the bucket to bypass Governance mode.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetBucketLocation",
"s3:GetObject",
"s3:PutObject",
"s3:DeleteObject",
"s3:GetBucketVersioning",
"s3:GetBucketObjectLockConfiguration",
"s3:ListBucketVersions",
"s3:GetObjectVersion",
"s3:GetObjectRetention",
"s3:GetObjectLegalHold",
"s3:PutObjectRetention",
"s3:PutObjectLegalHold",
"s3:DeleteObjectVersion"
],
"Resource": [
"arn:aws:s3:::myimmutablebucket/*"
]
},
{
"Effect": "Allow",
"Action": [
"s3:ListAllMyBuckets",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::myimmutablebucket/*"
]
}
]
}Reference: https://www.veeam.com/kb3151
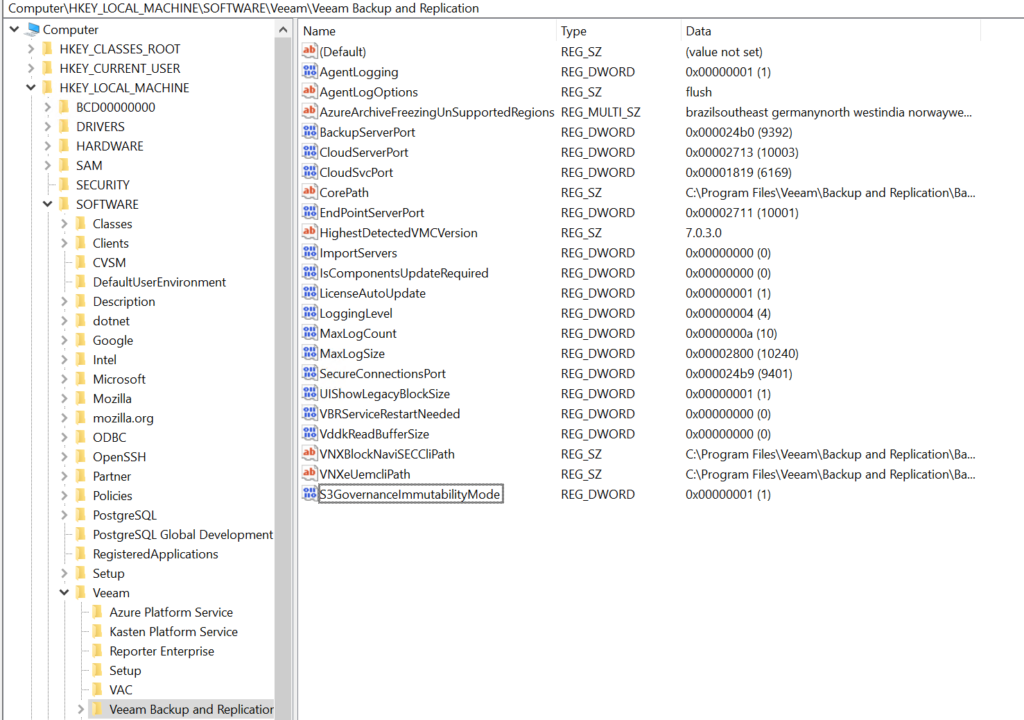
Veeam Registry Key
To allow Veeam to use Governance Mode, you need to add a special DWORD registry key.
HKEY_LOCAL_MACHINE\SOFTWARE\Veeam\Veeam Backup and Replication\S3GovernanceImmutabilityModeSet the value to 1.
Minio – Deleting the Data
From a Minio Perspective, you can delete the data in the entire bucket using the following command.
WARNING, this will delete *all* data within that bucket. This is not VM or backup job dependent. Don’t use unless you want to empty out the entire bucket.
mc rm --force -r --versions --bypass <alias>/myimmutablebucket/Veeam/Conclusion
If you’re not a service provider, you probably don’t care. However, if you are sending your backups offsite to some service provider, they are going to care, and you will want to know if its possible to remove your data from their systems, even if you use immutability.
Woah governance mode is a game changer! Super cool thanks for sharing.
It really is the best of both worlds!